Monitoring pfSense with Wazuh: A Comprehensive Guide
There are several ways to integrate pfSense with Wazuh. The easiest method is syslog, but you can also use the Wazuh agent. Wazuh agent (native package for pfSense) is already pre-installed In pfSense which is available in Yandex Cloud Marketplace/VK Cloud Marketplace. Therefore, you can start setting up immediately, bypassing the installation process.
Configuration
- First, you need to enable agent autorun. Edit the
/etc/rc.conf.localfile and replace stringwazuh_agent_enable="NO"with stringwazuh_agent_enable="YES". Alternatively, run the following command:
sysrc -f /etc/rc.conf.local wazuh_agent_enable="YES"- Next, configure the agent’s connection to the Wazuh Cluster. Edit the
/var/ossec/etc/ossec.conffile and replace the IP line with the IP address or FQDN of the Wazuh cluster.
<client>
<server>
<address>IP</address>
</server>
<config-profile></config-profile>
<crypto_method>aes</crypto_method>
</client>- The next step is to launch the agent by executing the command:
service wazuh-agent startIt is recommended to configure a cron task to automatically clear agent logs to optimize disk space usage (for example, older than 30 days). For this run the command:
crontab -eAn example of the cleanup command:
0 4 * * * find /var/ossec/logs/ossec/ -d 1 -mtime +30 -type d -exec rm -rf {} \; > /dev/nullThe agent should register with Wazuh after starting it. Check it by connecting to the Wazuh master via SSH and executing the following command:
cd /var/ossec/bin/
./agent_control -l If configured correctly, there is the state of pfSense as ‘Active’:
Wazuh agent_control. List of available agents:
ID: 000, Name: wazuh (server), IP: 127.0.0.1, Active/Local
ID: 001, Name: pfsense.ru-central1.internal, IP: any, ActiveAlso, the new agent will be in the Wazuh web interface (see Figure 1).
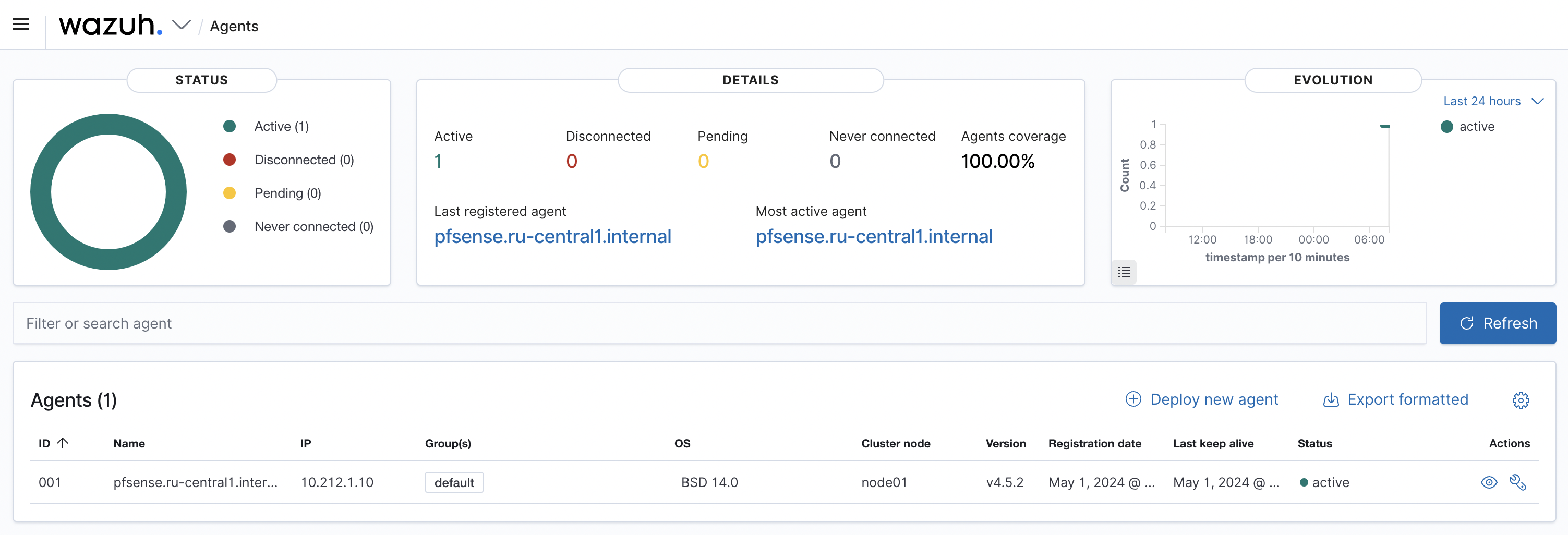
Figure 1. The Wazuh web Interface With the new Agent
The initial setup is complete, now you need to change Wazuh.
Configuring Suricata in pfSense with sending logs to Wazuh
First, you need to install Suricata
The next two parameters should be set as you can see at Figure 2.
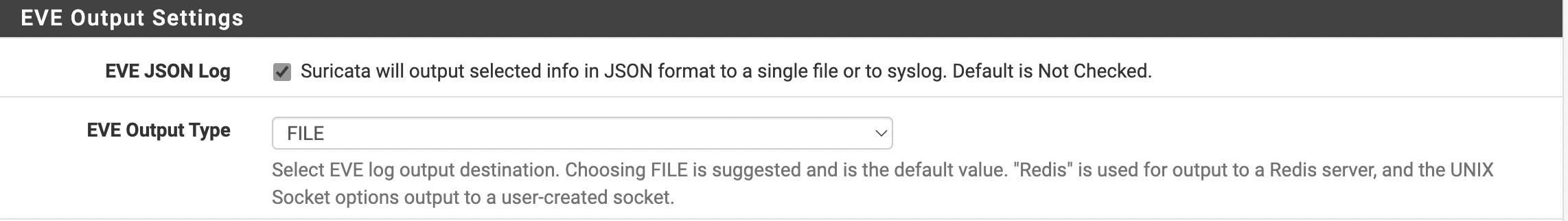
Figure 2. EVE Output Settings
- EVE Json Log - checked.
- EVE Output Type - “File.
The rest of the eve.json parameters can be set at the user’s preference during configuration.
- For Wazuh to start analyzing events from Suricata, the following lines must be added to the
/var/ossec/etc/ossec.confconfiguration file:
<localfile>
<log_format>json</log_format>
<location>/var/log/suricata/*/eve.json</location>
</localfile>Then restart the agent:
service wazuh-agent restartThe initial setup is complete, now you need to change Wazuh.
Configuring for firewall logs
Add the following lines to the /var/ossec/etc/ossec.conf configuration file:
<localfile>
<log_format>syslog</log_format>
<location>/var/log/filter.log</location>
</localfile>Then restart the agent.
The default pfSense firewall discard event rule is not logged, as specified by the line <options>no_log</options> in the rule
declaration.
If multiple requests are made from a single source by the pfSense firewall, the blocking event will be logged by default. If you want the blocking event from the pfSense firewall to be logged in Wazuh, you can change this. The following shows how to do this.
Create a custom rules file
- Open the Wazuh menu and and navigate
Management > Rules(see Figure 3).
Figure 3. Wazuh Control Panel
- Find rules for pfSense (see Figure 4).
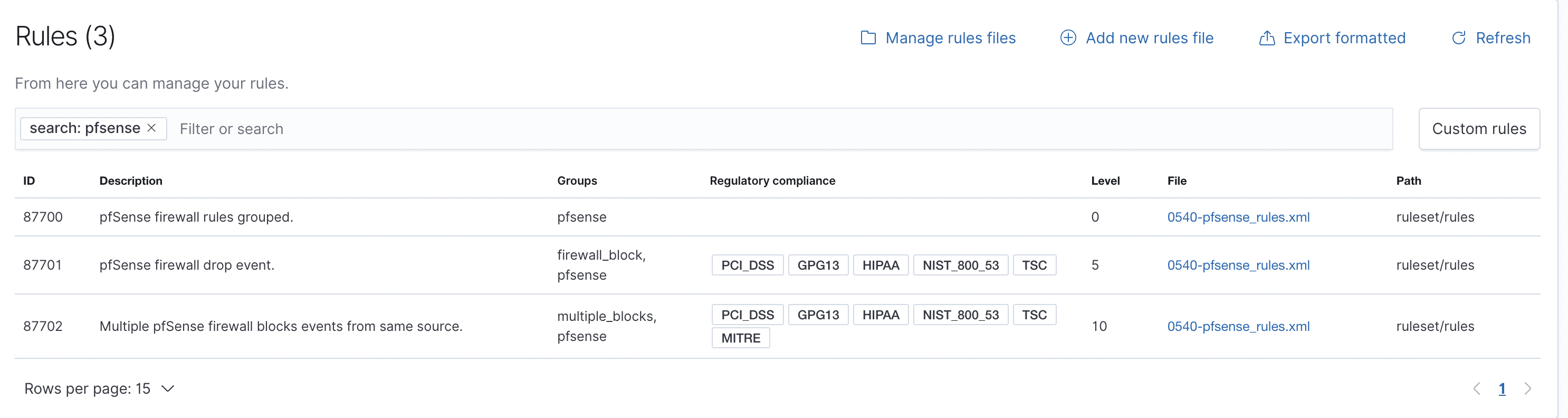
List Rules
- Click to open the rules in the
0540-pfsense_rules.xmlfile and copy the contents
<group name="pfsense,">
<rule id="87700" level="0">
<decoded_as>pf</decoded_as>
<program_name>filterlog</program_name>
<description>pfSense firewall rules grouped.</description>
</rule>
<!-- We don't log firewall events, because they go
- to their own log file.
-->
<rule id="87701" level="5">
<if_sid>87700</if_sid>
<action>block</action>
<options>no_log</options>
<description>pfSense firewall drop event.</description>
<group>firewall_block,pci_dss_1.4,gpg13_4.12,hipaa_164.312.a.1,nist_800_53_SC.7,tsc_CC6.7,tsc_CC6.8,</group>
</rule>
<rule id="87702" level="10" frequency="18" timeframe="45" ignore="240">
<if_matched_sid>87701</if_matched_sid>
<same_source_ip />
<description>Multiple pfSense firewall blocks events from same source.</description>
<mitre>
<id>T1110</id>
</mitre>
<group>multiple_blocks,pci_dss_1.4,pci_dss_10.6.1,gpg13_4.12,hipaa_164.312.a.1,hipaa_164.312.b,nist_800_53_SC.7,nist_800_53_AU.6,tsc_CC6.7,tsc_CC6.8,tsc_CC7.2,tsc_CC7.3,</group>
</rule>
</group>- Navigate to the previous screen and select “Add new rules file”. The file name can be anything you like, for example, “custom-pfSense-overrides.xml”. The following is a sample of its contents:
<group name="pfsense,">
<rule id="87700" level="0">
<decoded_as>pf</decoded_as>
<program_name>filterlog</program_name>
<description>pfSense firewall rules grouped.</description>
</rule>
<!-- We don't log firewall events, because they go
- to their own log file.
-->
<rule id="87701" level="5" overwrite="yes">
<if_sid>87700</if_sid>
<action>block</action>
<description>pfSense firewall drop event.</description>
<group>firewall_block,pci_dss_1.4,gpg13_4.12,hipaa_164.312.a.1,nist_800_53_SC.7,tsc_CC6.7,tsc_CC6.8,</group>
</rule>
<rule id="87702" level="10" frequency="18" timeframe="45" ignore="240">
<if_matched_sid>87701</if_matched_sid>
<same_source_ip />
<description>Multiple pfSense firewall blocks events from same source.</description>
<mitre>
<id>T1110</id>
</mitre>
<group>multiple_blocks,pci_dss_1.4,pci_dss_10.6.1,gpg13_4.12,hipaa_164.312.a.1,hipaa_164.312.b,nist_800_53_SC.7,nist_800_53_AU.6,tsc_CC6.7,tsc_CC6.8,tsc_CC7.2,tsc_CC7.3,</group>
</rule>
</group>In the example above, we removed <option>no_log</option> and added overwrite for the rule.
- Then press Save and Restart (see Figure 5).
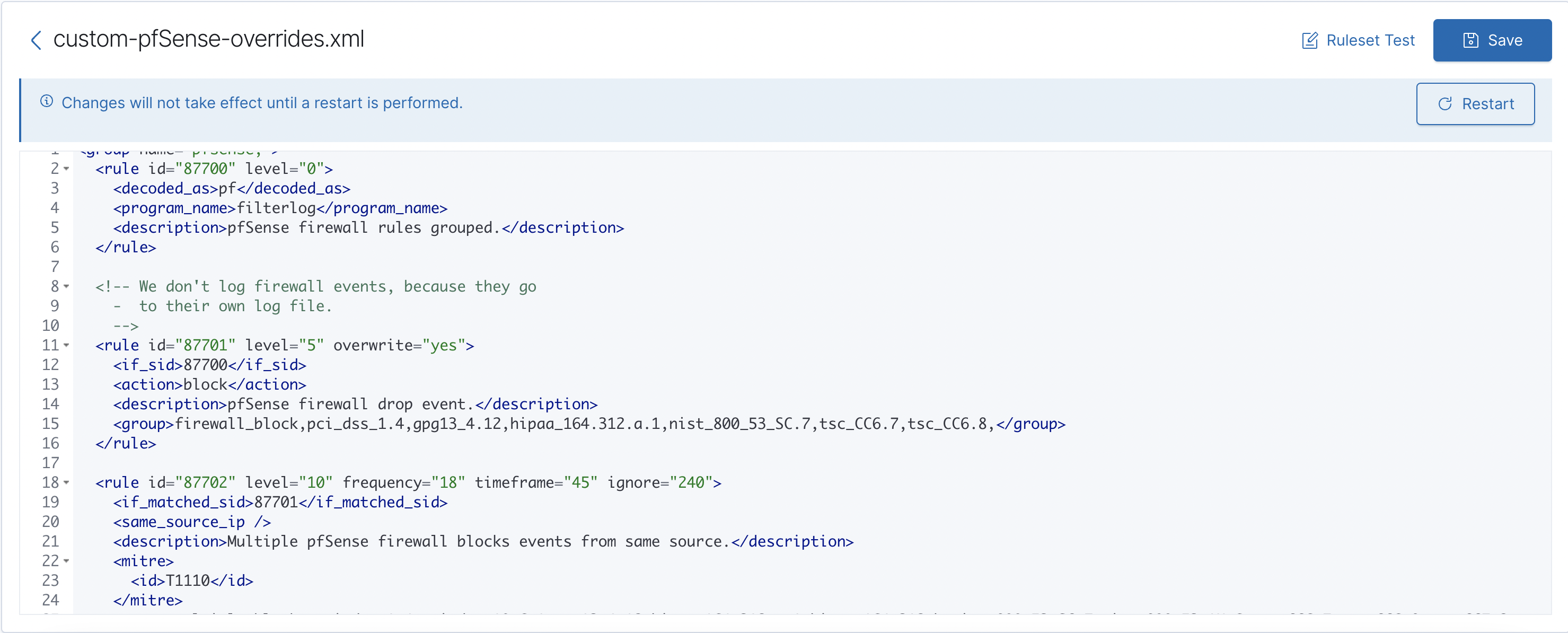
Figure 5. Save and Settings Window
- It is necessary to confirm the applied settings (see Figure 6).
Figure 6. Settings Applied Confirmation Window
You will now receive firewall events for the Wazuh agent on pfSense (see Figure 7).
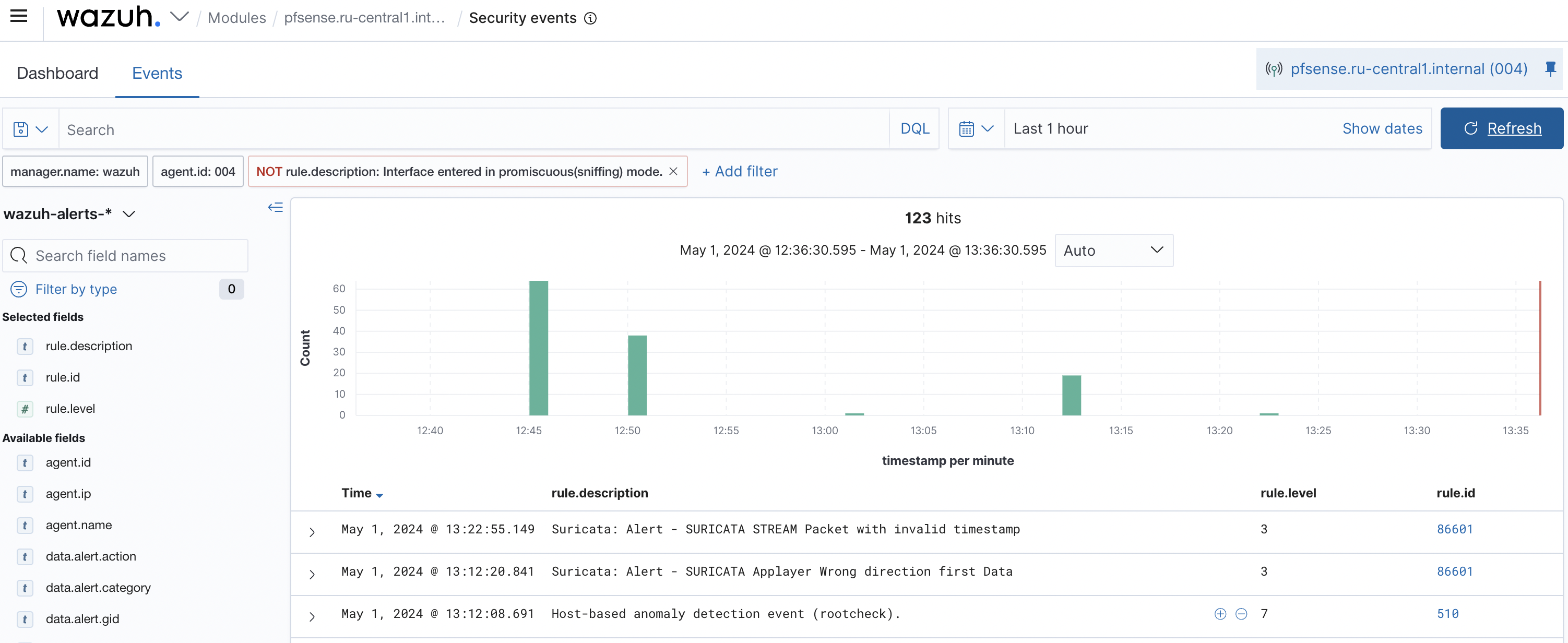
Figure 7. Security Events Window
Configuration is complete.