Snort and pfSense integration
Snort is one of the most well-known and widely used tools for detecting network attacks and intrusions (Intrusion Detection System (IDS). It is an open-source software designed to monitor network traffic and detect anomalous or malicious behavior on the network. Snort uses a set of rules to analyze network traffic and detect suspicious or malicious activities such as port scans, vulnerability attacks, and other types of network attacks. It can be configured to detect and block such attacks, making it a useful tool for protecting computer networks from intrusions and cyberattacks.
Install Snort in pfSense
To install Snort, open the pfSense web interface and navigate to “System –> Package Manager –> Available Packages”. The user should type “snort” in the search bar (see Figure 1).
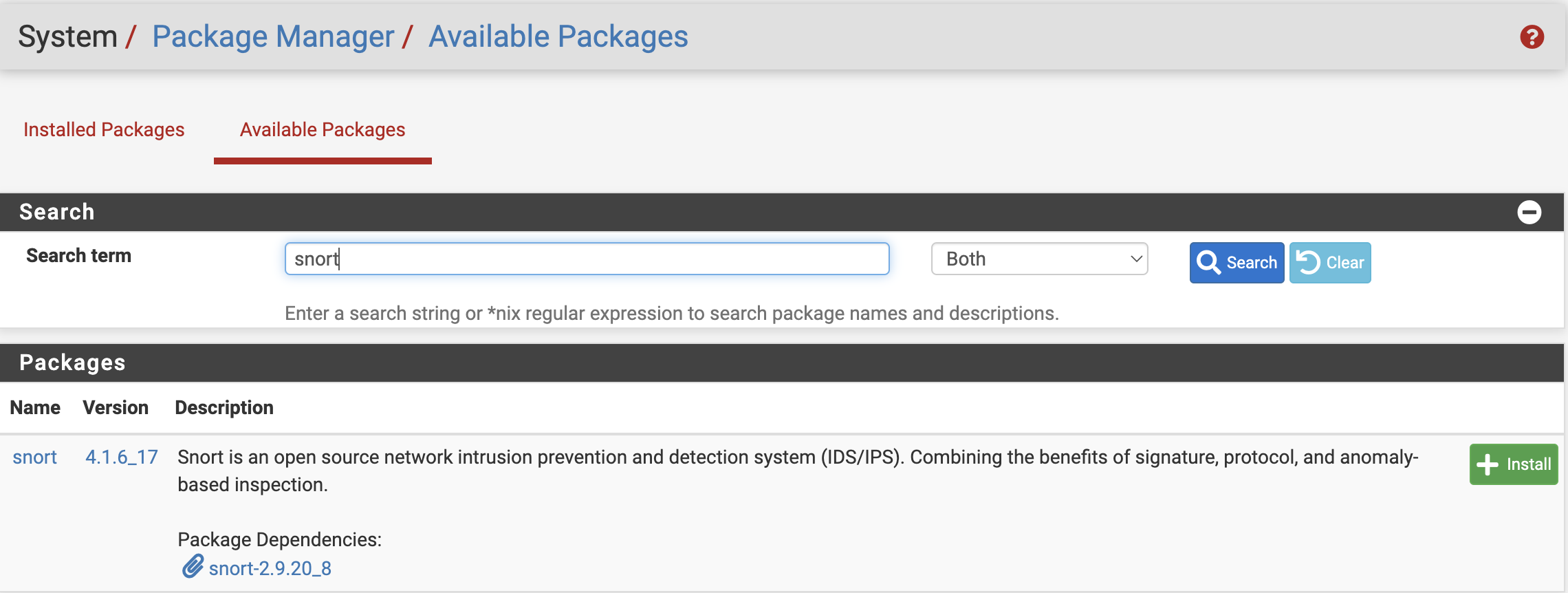
Figure 1. Installing Snort
After these, Snort will appear in the list of packages. The user should click “Install” and wait for the installation process to complete (see Figure 2).
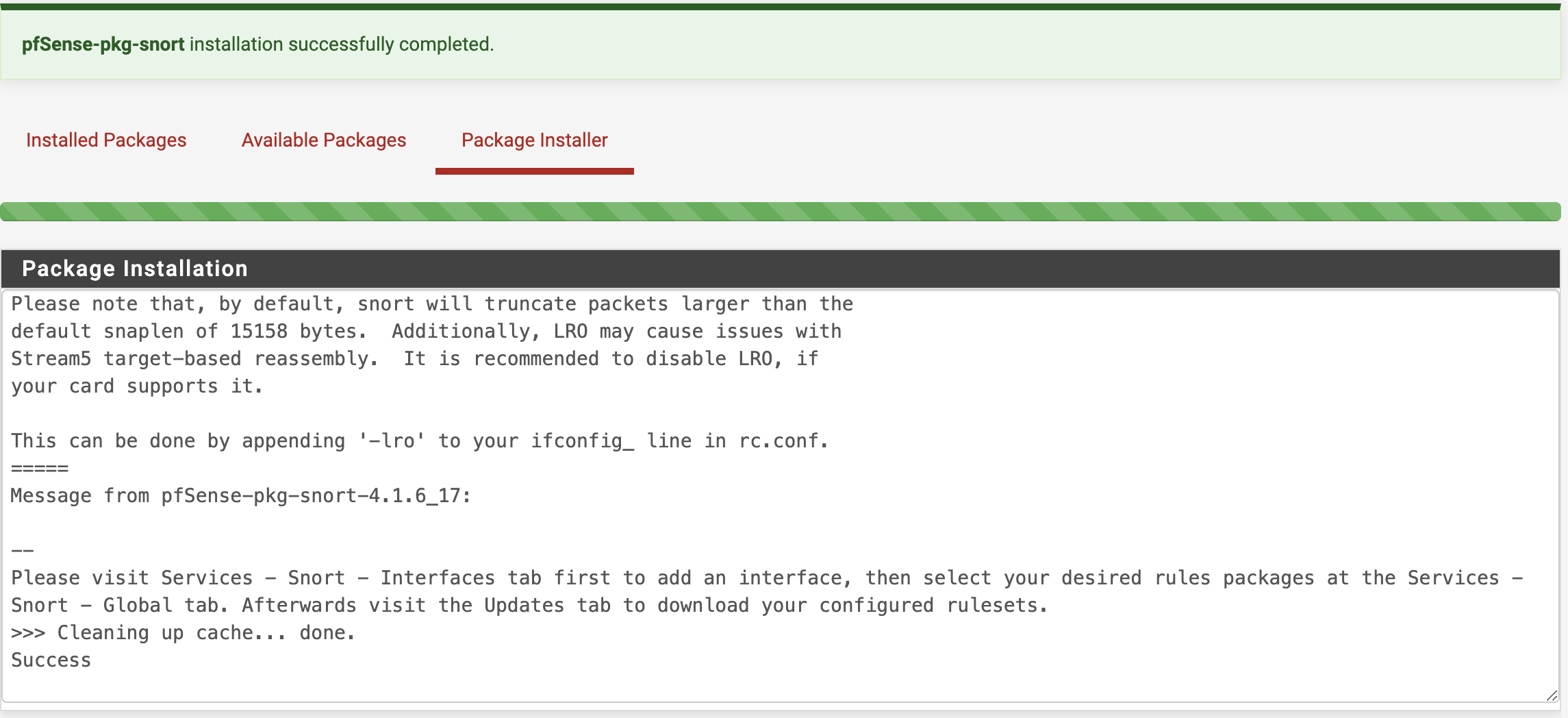
Figure 2. Completing the Snort Installation
Configuring Snort
- The first step is for the user to go to Services -> Snort.
The users should start the configuration from Global Settings:
- Snort Subscriber Rules - Select if you have a subscription and Snort Oinkmaster Code.
- Snort GPLv2 Community Rules - Check the box for “Snort GPLv2 Community Rules”.
- Emerging Threats (ET) Rules - check the box for “Enable ET Open”.
- Sourcefire OpenAppID Detectors- check the box for “Enable OpenAppID”.
- FEODO Tracker Botnet C2 IP Rules - check the box for “Enable FEODO Tracker Botnet C2 IP Rules.”
- Rules Update Settings - set “Update Interval” equal to “1 DAY” and time as you wish.
After all the settings are done, the user needs to click on the Save button.
- The next step is to go to the Snort Interfaces section and create an interface for the sensor. The settings are left to the user’s preference. If for some reason it is impossible to update from the official snort servers, the user can use alternative mirrors. Configure mirror for rules
Configure mirror for rules
To download updates not from the official Snort site the user needs to make changes to the file:
/usr/local/pkg/snort/snort_defs.inc
To do this, open the file in edit mode and change snort.org to a third-party mirror. For example:
vi /usr/local/pkg/snort/snort_defs.incThe user needs to find the line “VRT_DNLD_URL”, “GPLV2_DNLD_URL”, “SNORT_OPENAPPID_DNLD_URL” and change it to their values.
An example of a complete change file is shown below:
snort_defs.inc
<?php
/*
* snort_defs.inc
*
* part of pfSense (https://www.pfsense.org)
* Copyright (c) 2006-2023 Rubicon Communications, LLC (Netgate)
* Copyright (c) 2009-2010 Robert Zelaya
* Copyright (c) 2013-2022 Bill Meeks
* All rights reserved.
*
* Licensed under the Apache License, Version 2.0 (the "License");
* you may not use this file except in compliance with the License.
* You may obtain a copy of the License at
*
* http://www.apache.org/licenses/LICENSE-2.0
*
* Unless required by applicable law or agreed to in writing, software
* distributed under the License is distributed on an "AS IS" BASIS,
* WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
* See the License for the specific language governing permissions and
* limitations under the License.
*/
global $g;
/* Define some useful constants for Snort */
if (!defined("SNORT_BASEDIR")) {
define("SNORT_BASEDIR", "/usr/local/");
}
if (!defined("SNORT_BINDIR"))
define("SNORT_BINDIR", SNORT_BASEDIR . "bin/");
if (!defined("SNORTDIR"))
define("SNORTDIR", SNORT_BASEDIR . "etc/snort");
if (!defined("SNORTLOGDIR"))
define("SNORTLOGDIR", "{$g['varlog_path']}/snort");
if (!defined("SNORT_BIN_VERSION")) {
// Grab the Snort binary version programmatically by
// running the binary with the command-line argument
// to display the version information.
$snortbindir = SNORT_BINDIR;
$snortver = exec_command("{$snortbindir}/snort -V 2>&1 |/usr/bin/grep Version | /usr/bin/cut -c20-31");
// Extract just the numbers and decimal point
// delimiters at the front of the version string.
$matches = array();
if (preg_match('/^[^\s]+/', $snortver, $matches)) {
define("SNORT_BIN_VERSION", $matches[0]);
}
else {
define("SNORT_BIN_VERSION", "2.9.20");
}
}
if (!defined("SNORT_SID_MODS_PATH"))
define('SNORT_SID_MODS_PATH', "{$g['vardb_path']}/snort/sidmods/");
if (!defined("SNORT_IPREP_PATH"))
define("SNORT_IPREP_PATH", "{$g['vardb_path']}/snort/iprep/");
if (!defined('SNORT_APPID_ODP_PATH'))
define('SNORT_APPID_ODP_PATH', SNORTDIR . "/appid/");
if (!defined('SNORT_APPID_RULES_PATH'))
define('SNORT_APPID_RULES_PATH', SNORTDIR . "/rules/");
// Rules filenames, download URLs and prefixes.
// Be sure to include the trailing backslash on URLs.
if (!defined("SNORT_ENFORCING_RULES_FILENAME"))
define("SNORT_ENFORCING_RULES_FILENAME", "snort.rules");
if (!defined("FLOWBITS_FILENAME"))
define("FLOWBITS_FILENAME", "flowbit-required.rules");
if (!defined("SNORT_RULES_UPD_LOGFILE"))
define("SNORT_RULES_UPD_LOGFILE", SNORTLOGDIR . "/snort_rules_update.log");
if (!defined("VRT_DNLD_URL"))
define("VRT_DNLD_URL", "https://snort.comcloud.xyz/rules/");
if (!defined("ET_VERSION"))
define("ET_VERSION", "2.9.0");
if (!defined("ET_BASE_DNLD_URL"))
define("ET_BASE_DNLD_URL", "https://rules.emergingthreats.net/");
if (!defined("ETPRO_BASE_DNLD_URL"))
define("ETPRO_BASE_DNLD_URL", "https://rules.emergingthreatspro.com/");
if (!defined("SNORT_ET_DNLD_FILENAME"))
define("SNORT_ET_DNLD_FILENAME", "emerging.rules.tar.gz");
if (!defined("SNORT_ETPRO_DNLD_FILENAME"))
define("SNORT_ETPRO_DNLD_FILENAME", "etpro.rules.tar.gz");
if (!defined("SNORT_GPLV2_DNLD_FILENAME"))
define("SNORT_GPLV2_DNLD_FILENAME", "community-rules.tar.gz");
if (!defined("GPLV2_DNLD_URL"))
define("GPLV2_DNLD_URL", "https://snort.comcloud.xyz/downloads/community/");
if (!defined("SNORT_OPENAPPID_DNLD_URL"))
define("SNORT_OPENAPPID_DNLD_URL", "https://snort.comcloud.xyz/downloads/openappid/");
if (!defined("SNORT_OPENAPPID_DNLD_FILENAME"))
define("SNORT_OPENAPPID_DNLD_FILENAME", "snort-openappid.tar.gz");
if (!defined("SNORT_OPENAPPID_RULES_URL"))
define("SNORT_OPENAPPID_RULES_URL", "https://files.netgate.com/openappid/");
if (!defined("SNORT_OPENAPPID_RULES_FILENAME"))
define("SNORT_OPENAPPID_RULES_FILENAME", "appid_rules.tar.gz");
if (!defined("SNORT_RULES_UPD_LOGFILE"))
define("SNORT_RULES_UPD_LOGFILE", SNORTLOGDIR . "/snort_rules_update.log");
if (!defined("VRT_FILE_PREFIX"))
define("VRT_FILE_PREFIX", "snort_");
if (!defined("GPL_FILE_PREFIX"))
define("GPL_FILE_PREFIX", "GPLv2_");
if (!defined("ET_OPEN_FILE_PREFIX"))
define("ET_OPEN_FILE_PREFIX", "emerging-");
if (!defined("ET_PRO_FILE_PREFIX"))
define("ET_PRO_FILE_PREFIX", "etpro-");
if (!defined("OPENAPPID_FILE_PREFIX"))
define("OPENAPPID_FILE_PREFIX", "openappid-");
if (!defined("FEODO_TRACKER_DNLD_FILENAME"))
define("FEODO_TRACKER_DNLD_FILENAME", "feodotracker.tar.gz");
if (!defined("FEODO_TRACKER_DNLD_URL"))
define("FEODO_TRACKER_DNLD_URL", "https://feodotracker.abuse.ch/downloads/");
?>